What is personally identifiable information (PII)? A guide to protecting sensitive data

When you sign up for an online service, you usually provide details like your name, email address, phone number, and even payment information. All of this is known as personally identifiable information (PII): data that can be used to identify you.
In this guide, we’ll explain what qualifies as PII, why it’s important for your privacy and security, and how you can keep it safe from misuse.
Please note: This information is for general educational purposes and not financial or legal advice.
What is PII, and why does it matter?
PII refers to any information that can be used to identify a person, either directly or indirectly. Some details, like your full name or Social Security number (SSN), reveal your identity right away. Others, such as your email address or location history, only identify you when combined with other data. This still counts as PII.
Protecting PII is essential because once it’s exposed, cybercriminals can exploit it for identity theft, phishing, or social engineering. For example, in 2015, the Internal Revenue Service (IRS) reported that attackers were able to access about 100,000 taxpayer accounts by piecing together information from other sources and answering verification questions meant only for the taxpayers.
By understanding what qualifies as PII, you can take steps to protect your privacy and lower the risk of online threats.
What are the 10 most common types of PII?
PII covers many types of information, but some appear more often in daily use. Below are 10 of the most common examples:
- Full name
- Email address
- Phone number
- SSN
- Passport number
- Driver’s license
- Date of birth
- Login credentials
- Biometric data
- Employment information
Financial details, such as bank accounts or credit cards, also fall under PII. The same goes for medical information, including health records, insurance data, and prescriptions.
What is not included in PII?
Data that is anonymized, aggregated, or stripped of unique identifiers generally isn’t PII, since it can’t be used on its own to trace or identify someone. Examples of non-PII include:
- Aggregated statistics, such as average website visitor age.
- Masked or partially masked IP addresses.
- General details like job titles, company names, or the name of a city.
It’s important to note that what counts as PII can vary depending on local laws and regulations.
How PII is classified, and why context matters
You’ll often find different ways of classifying PII. Some sources distinguish between direct and indirect identifiers and sensitive and non-sensitive PII. These categories can be useful for understanding how data relates to identity, but in practice, their lines are almost always blurred. What truly matters is context: how, where, and with what other information the data is used.
For example, a person’s full name is often listed as a “direct identifier,” meaning it can supposedly identify someone on its own. But that’s not always true. If your name is John Smith or Maria García, it’s shared by thousands of people. On its own, it doesn’t necessarily identify you.
The same applies to sensitive vs. non-sensitive PII. Information that seems harmless in one situation can become sensitive in another. A list of employee names might not be sensitive if it’s from a company’s public website. But the same list becomes sensitive if it shows which employees failed a mandatory training or belong to a specific medical program.
In other words, sensitivity isn’t an absolute quality of the data: it depends on how the information could affect someone if exposed.
Examples of how context changes data sensitivity
| Data type | Usually not sensitive | Becomes sensitive when… |
| Name | Appears in a conference attendee list | Appears in a list of hospital patients or police officers |
| Email address | Used for work-related contact | Linked to personal accounts or health information |
| Job title | Listed on a company website | Reveals involvement in classified or investigative work |
| Date of birth | Used for demographic statistics | Combined with name and ZIP code, making someone identifiable |
| Photo | Posted on social media voluntarily | Used without consent in a sensitive or compromising context |
Why PII needs to be protected
When PII is exposed, stolen, or shared without consent, it can have lasting consequences for both individuals and organizations.
At the individual level, leaked PII can lead to identity theft, financial fraud, and unauthorized account access. Stolen financial details can be used for unauthorized purchases or to drain accounts. Leaked personal details can be used to stalk, blackmail, or spread false information. In some cases, location or household data can put people at risk of physical harm. Taking steps toward identity theft prevention can reduce these risks and help keep your personal information secure.
For organizations, the risks are equally serious. Mishandling PII can cause data breaches, loss of customer trust, and legal penalties under privacy laws such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). Even accidental disclosures, like sending an email with unredacted personal details, can trigger compliance issues and reputational damage.
Common methods of PII theft
Malicious actors use many techniques to obtain personal data, often exploiting weak security or human error:
- Phishing: Fraudulent emails, texts, or sites that trick people into revealing credentials or financial data.
- Social engineering and impersonation: Manipulating people or support systems to disclose or reset access to accounts.
- Data breaches: Poorly secured databases that leak large volumes of personal information.
- Malware: Software that captures keystrokes, exfiltrates files, or harvests stored credentials.
- Unsafe Wi-Fi and man-in-the-middle (MITM) attacks: Public networks can let attackers intercept unencrypted traffic.
- Insider threats and data brokers: Authorized users or third parties can expose or sell data, intentionally or accidentally.
How to protect yourself from PII theft
Strong cybersecurity and physical security measures can significantly reduce the risk of PII theft.
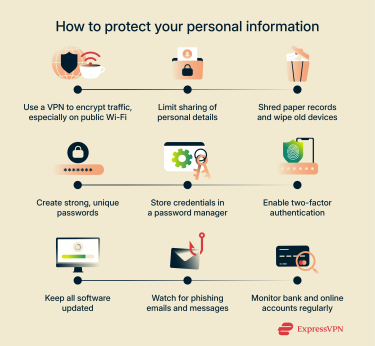
- Use a virtual private network (VPN): ExpressVPN encrypts your internet traffic and masks your IP address, helping keep your data more private. Its Identity Defender (available to U.S. users on select plans) can also remove your details from data broker sites and alert you to changes in your credit score or if your personal details appear on the dark web.
- Limit what you share: Provide details like your SSN, home address, or phone number only when necessary and only to trusted parties.
- Safely dispose of sensitive data: Shred documents containing personal information before discarding them to prevent reconstruction or misuse.
- Use strong and unique passwords: Create a different password for each account and make them difficult to guess. A trustworthy password manager like ExpressKeys can securely generate and store complex passwords so you don’t have to remember them all.
- Enable two-factor authentication (2FA): Add an extra verification step, such as a one-time code or biometric login, for stronger protection.
- Keep software up to date: Regularly update your operating system, browser, and other software to patch security vulnerabilities.
- Be cautious of unknown emails: Avoid clicking links or providing personal information in suspicious messages.
- Limit what you do on public Wi-Fi networks: Don’t access sensitive accounts on unsecured networks; use a VPN if you must connect.
- Monitor your accounts: Check bank, credit card, and online accounts frequently for unusual activity.
 For businesses and teams, employee training is crucial. Staff should know how to recognize phishing and handle or dispose of PII securely, both online and offline.
For businesses and teams, employee training is crucial. Staff should know how to recognize phishing and handle or dispose of PII securely, both online and offline.
Legal protections and data privacy laws around PII
PII is protected under various laws worldwide, which aim to prevent misuse, enforce accountability, and grant individuals rights over their personal data. Knowing these laws helps you understand both your rights and the obligations of organizations that handle your information.
U.S. and state-level privacy laws
In the U.S., federal and state laws provide varying levels of protection. The Federal Trade Commission (FTC) has authority to act against unfair or deceptive practices involving consumer data under its consumer protection mandate.
Laws such as the California Consumer Privacy Act (CCPA) give residents rights to know what data companies collect and to opt out of its sale. Other states are increasingly passing their own privacy laws (e.g., Virginia, Colorado), but coverage, rights, enforcement, and exemptions differ.
International privacy regulations
Many countries legislate rules for how organizations collect, process, store, and share personal data:
- The European Union’s General Data Protection Regulation (GDPR): Sets a high bar for data protection, including requirements for consent, data subject rights, and significant penalties for noncompliance.
- Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA): Governs how private-sector organizations collect, use, and disclose personal information in the course of commercial activities. It grants individuals rights such as access and correction.
- Australia’s Privacy Act 1988: Regulates the handling of personal information by government agencies and certain private organizations. It includes rights to access and correct personal information.
Brazil’s Data Protection Law and Japan’s Act on the Protection of Personal Information (APPI) are also major modern privacy frameworks enforcing rules on how personal data is managed in those nations.
Industry-specific compliance
Some industries have specialized laws that provide additional protection or regulation over specific kinds of PII. For example, healthcare organizations in the U.S. must comply with the Health Insurance Portability and Accountability Act (HIPAA), which protects patient information. Educational institutions follow the Family Educational Rights and Privacy Act (FERPA), giving parents and students access to education records and the ability to correct them while restricting who can view them without permission. The Gramm-Leach-Bliley Act (GLBA) applies to financial institutions, requiring them to explain their information-sharing practices, safeguard customer data, and notify customers of their privacy policies.
FAQ: Common questions about PII
What is considered personally identifiable information?
Personally identifiable information (PII) includes any data that can identify an individual. This ranges from direct identifiers like your Social Security number (SSN) or passport number to indirect identifiers such as your birthdate, ZIP code, or job title, which need to be combined with other data to identify an individual.
What is the difference between personal data and PII?
Personal data and personally identifiable information (PII) are related but slightly different concepts. PII is a term commonly used in the U.S. that refers to information that identifies an individual. Personal data is a broader term used internationally, including under regulations like the General Data Protection Regulation (GDPR), covering any data related to an identifiable person, even if it doesn’t directly identify them. Essentially, all PII is personal data, but not all personal data qualifies as PII.
What is an example of PII?
An example of personally identifiable information (PII) is your Social Security number (SSN) or email address. These pieces of information can directly identify you or be combined with other data to reveal your identity. Other examples include phone numbers, biometric data, login credentials, or passport numbers. Recognizing common examples helps you understand what to protect in your daily digital activities.
What is not considered PII?
Data that can’t be traced back to a specific individual is generally not considered personally identifiable information (PII). This includes anonymized, aggregated, or statistical information, such as the average age of website visitors or anonymized survey responses. While this information can be useful for analysis, it doesn’t reveal personal identities on its own and carries a lower privacy risk.
What happens if my PII is exposed?
If your personally identifiable information (PII) is exposed, it can be used for identity theft, phishing, or fraud. Malicious actors may open accounts in your name, attempt to access online accounts, or craft targeted scams using your personal details. Early detection and preventive steps, such as monitoring accounts and using privacy tools like ExpressVPN’s Identity Defender, may reduce the likelihood of serious consequences.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN