What is SSTP (Secure Socket Tunneling Protocol)? Complete guide
There are numerous VPN protocols to choose from when you want to establish a secure connection and encrypt your online data, including OpenVPN and WireGuard.
SSTP, or Secure Socket Tunneling Protocol, isn’t quite as well-known or widespread, but it’s still worth learning about. Developed by Microsoft, it works particularly well on Windows devices and can be a practical, efficient choice in some settings, blending convenience with security.
This guide explores what SSTP is, how it works, and how it compares to other VPN protocols.
What is SSTP?
SSTP is a VPN protocol that was developed by Microsoft and released in 2007 alongside Windows Vista. Like other VPN protocols, it’s designed to create a secure tunnel between a user’s device and a VPN server, allowing encrypted data to flow safely and privately from one end to the other.
Microsoft made SSTP to replace the older and less secure Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) protocols.
How does SSTP work?
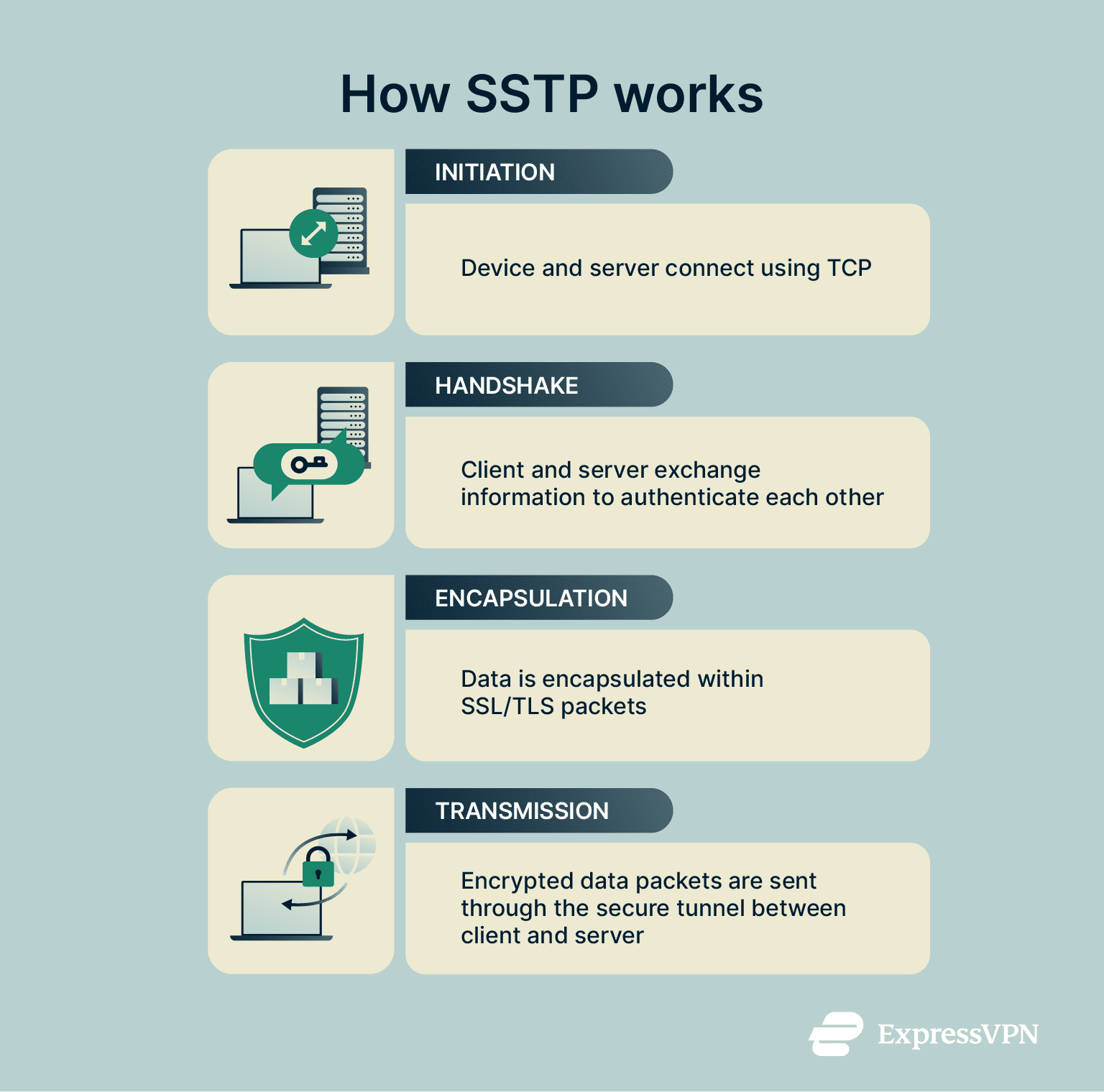 SSTP works by forming a secure tunnel between the user or client and the server before transmitting encrypted data packets through that tunnel. The next sections will take a closer look at how this happens and the various protocols and systems involved in securing SSTP connections and data.
SSTP works by forming a secure tunnel between the user or client and the server before transmitting encrypted data packets through that tunnel. The next sections will take a closer look at how this happens and the various protocols and systems involved in securing SSTP connections and data.
How SSTP encryption and security layers protect data
SSTP encrypts data and forms a secure VPN connection following a simple step-by-step process:
- Initiation: The client device first establishes a Transmission Control Protocol (TCP) connection to the VPN server, using port 443.
- Handshake/Authentication: The client and server carry out a Secure Sockets Layer (SSL) / Transport Layer Security (TLS) handshake, during which the server’s certificate is verified to authenticate the server. This handshake negotiates cryptographic keys that will secure the session. The client may then authenticate itself using a username/password combination or a client certificate.
- Encapsulation: With a secure channel established between client and server, Point-to-Point Protocol (PPP) data packets are then encapsulated within SSL/TLS packets.
- Transmission: The encapsulated packets are sent through the secure tunnel from the client to the server.
Ports and network protocols used by SSTP connections
As far as ports are concerned, only one matters when it comes to SSTP connections: port 443. This is the same port typically used for TCP HTTPS traffic, meaning that SSTP VPN traffic effectively looks and operates just like regular secure web traffic. Sending VPN traffic over port 443 is considered a basic form of obfuscation (but not a very effective one by today’s standards).
SSTP connections wrap regular internet data, which is carried using the Point-to-Point Protocol (PPP) inside TLS, which is the same encryption technology used to secure websites.
The encrypted, encapsulated data is then sent through the secure tunnel using TCP, which is a reliable method of delivering information across the internet to make sure nothing gets lost on the way.
Operating system compatibility
Given that SSTP was created by Microsoft, many people mistakenly assume that it’s a Windows-exclusive protocol. That’s not the case, as third-party apps and workarounds have made it possible to use SSTP on a range of other platforms and operating systems, including Linux, macOS, and Android.
However, SSTP did start life as a Windows-only VPN protocol and was designed by Microsoft with the Windows ecosystem in mind. Because of that, even though it can work on other systems, it runs best on Windows machines and lacks the more convenient, universal compatibility of other VPN protocols.
How secure is SSTP?
Security is one of the top priorities for users when selecting a VPN protocol, and SSTP is widely considered to be a relatively secure protocol. This is thanks to the fact that it uses proven SSL/TLS security combined with 256-bit Advanced Encryption Standard (AES) encryption ciphers to establish a safe and secure connection between the user and the server.
However, SSTP is not considered the most secure of all VPN protocols. It has some weaknesses and limitations that users need to keep in mind. Here’s a closer look at its main strengths and vulnerabilities.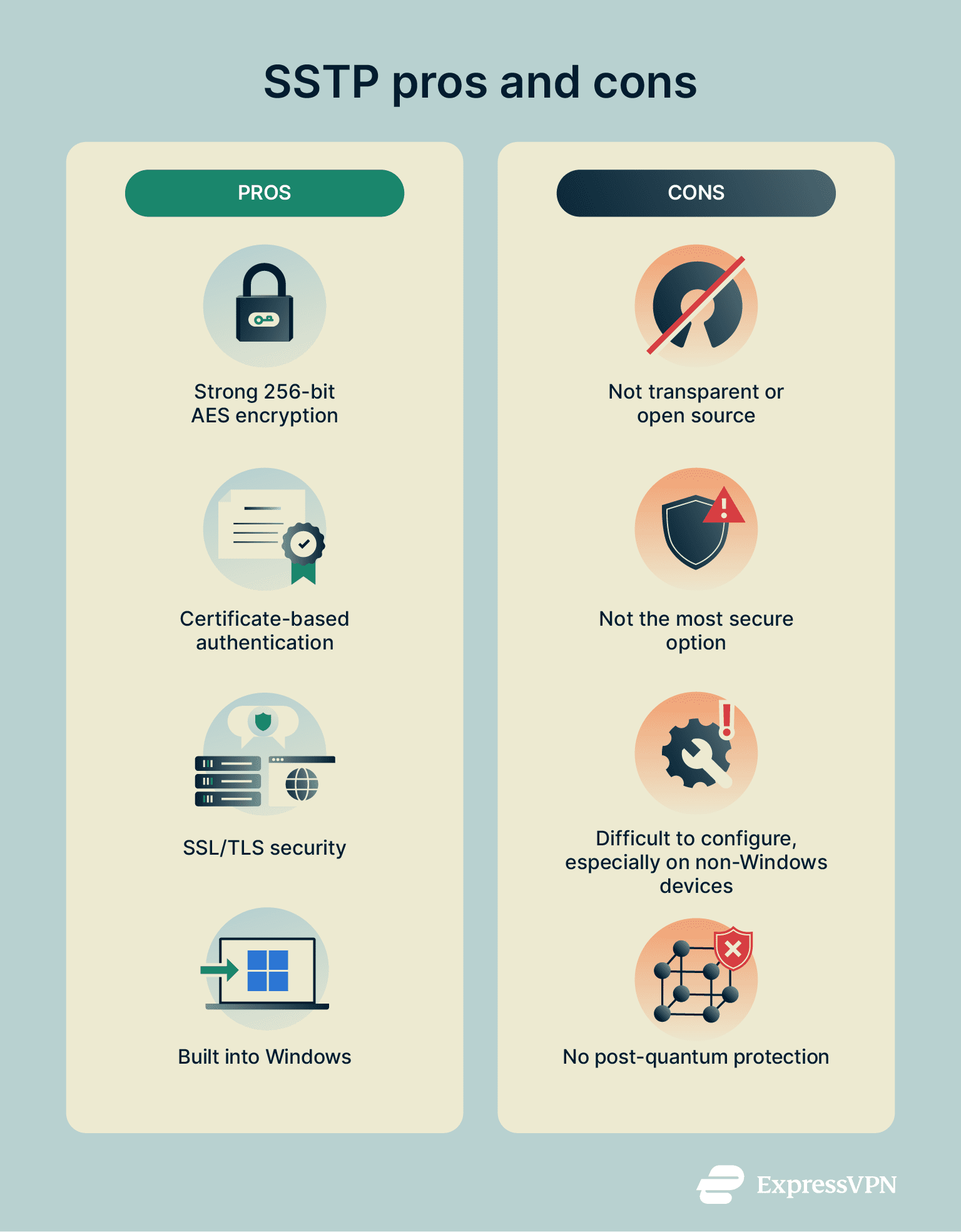
Strengths of SSTP encryption
- Strong encryption: SSTP uses 256-bit AES encryption, which is widely regarded as one of the strongest cryptographic algorithms available today.
- Certificate-based authentication: SSTP uses SSL certificates for authentication when connecting servers and clients, which helps to guard against certain cyberattacks, like man-in-the-middle (MITM) attacks.
- SSL/TLS security: SSTP follows the tried and tested SSL/TLS encryption framework to keep data safe, private, and effectively inaccessible for unauthorized users.
Limitations and vulnerabilities
- Not open source: Microsoft has not made the SSTP code open and available for auditing purposes, so it may have unknown vulnerabilities.
- Security varies: The level of security provided by SSTP depends on which version of TLS is being used.
- Misconfiguration risks: If SSTP isn’t configured correctly with the right cipher choices, user security may be compromised. This is even more likely on non-Windows platforms, as SSTP is generally harder to set up and use outside the Windows ecosystem.
- No post-quantum protection: SSTP doesn’t currently incorporate post-quantum cryptographic algorithms, which means it may be vulnerable to future quantum computing attacks.
SSTP vs. other VPN protocols
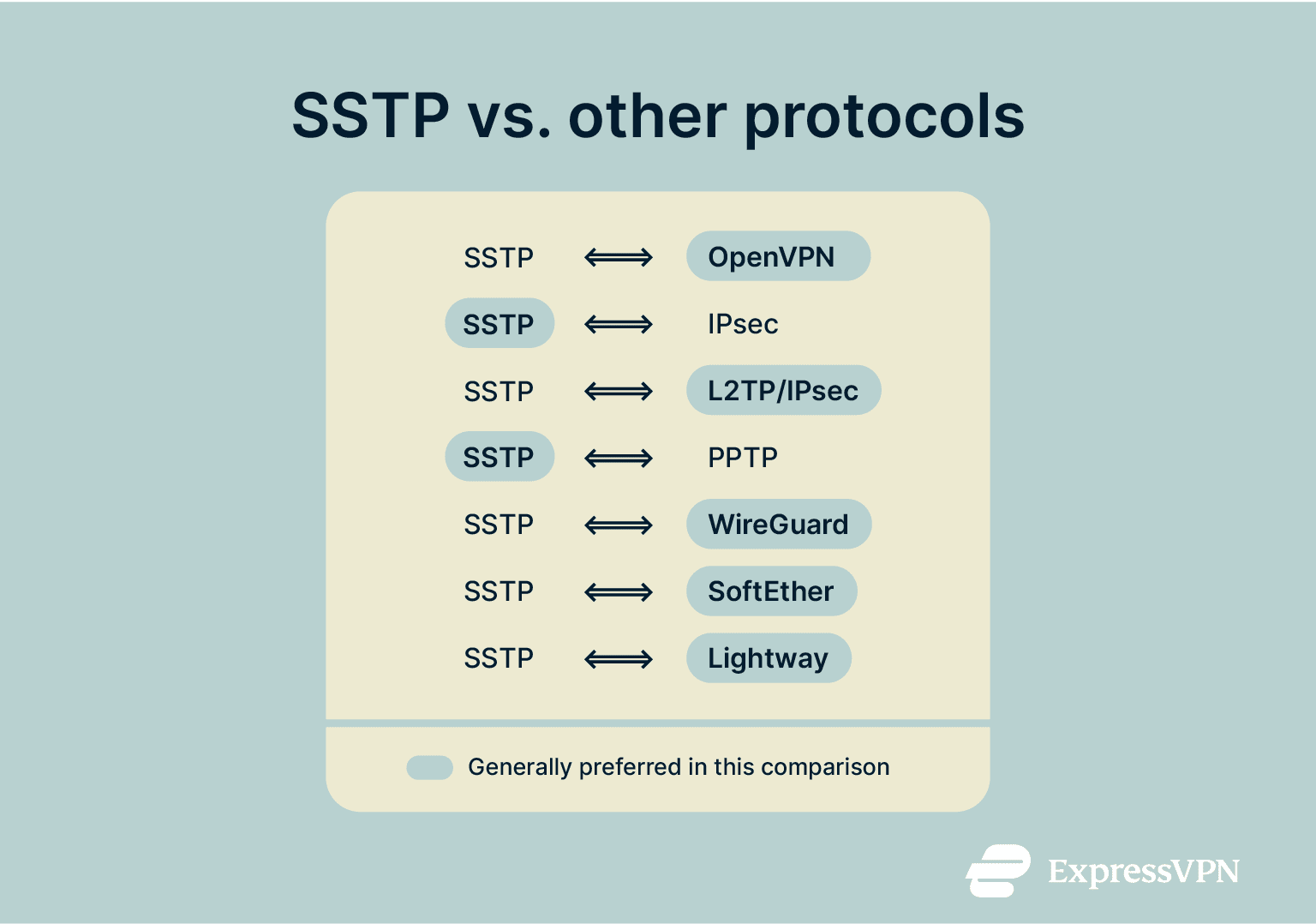 SSTP is far from the only VPN protocol available when you want to set up a secure VPN connection. Let’s take a closer look at how SSTP matches up against various other protocols.
SSTP is far from the only VPN protocol available when you want to set up a secure VPN connection. Let’s take a closer look at how SSTP matches up against various other protocols.
SSTP vs. OpenVPN
OpenVPN is an open-source VPN protocol, which instantly sets it apart from SSTP, which is closed-source. That means the code for OpenVPN is freely available for developers and cybersecurity experts to inspect and audit, while SSTP’s is not.
Because of this, even though OpenVPN and SSTP both use strong AES encryption methods, OpenVPN is considered more secure. OpenVPN also boasts superior compatibility, since it wasn't designed with only one operating system in mind, like SSTP was with Windows.
Plus, OpenVPN uses both User Datagram Protocol (UDP) and Transmission Control Protocol (TCP) protocols for faster speeds when transmitting encrypted data between clients and servers, making it a better choice for resource-heavy tasks like gaming, streaming, etc.
SSTP vs. IPsec
Internet Protocol Security (IPsec) is not a VPN protocol on its own but instead works alongside other protocols to establish VPN connections.
From a security perspective, both SSTP and IPsec are quite similar, though IPsec varies quite a lot depending on how it’s configured and demands a more careful approach to setup and management.
In terms of compatibility and performance, IPsec works well on a range of platforms, though it can have some issues when attempting to bypass firewalls or other network restrictions. SSTP, on the other hand, can be effective at bypassing firewalls because it uses port 443.
SSTP is also usually faster than IPsec, though this again depends on configuration specifics.
SSTP vs. L2TP/IPsec
SSTP is more modern and secure than Layer 2 Tunneling Protocol with Internet Protocol Security (L2TP/IPsec). It also tends to be quicker, since L2TP uses a double encapsulation process that can negatively impact connection speeds, as well as using more computing resources.
L2TP has a slight edge in compatibility, since it’s well-supported on a wide range of platforms, but SSTP is a better option in most cases (and especially on Windows machines).
SSTP vs. IKEv2/IPsec
SSTP and Internet Key Exchange version 2 with Internet Protocol Security (IKEv2/IPsec) have similar standards of security and share a similar history, with IKEv2 also being made by Microsoft, in conjunction with Cisco. This also means that, like SSTP, IKEv2 is not open source, though open variants of this protocol do exist, such as OpenIKEv2.
In terms of speed, IKEv2/IPsec typically runs faster than SSTP, thanks to its use of UDP for faster data transmission and Mobility and Multihoming Protocol (MOBIKE) technology that keeps the connection established, even if network conditions change. This makes IKEv2/IPsec a stronger choice on mobile platforms than SSTP.
However, SSTP has an advantage in environments where TCP traffic on port 443 is allowed, which can make it easier to bypass some firewalls compared with IKEv2, though it’s not guaranteed to bypass all firewall restrictions.
SSTP vs. PPTP
SSTP and Point-to-Point Tunneling Protocol (PPTP) have a lot in common, as they’re both Microsoft VPN protocols, though PPTP is significantly older.
Since SSTP is newer, it’s much stronger in the security department, using more advanced encryption algorithms and superior protection frameworks for secure data transmission. PPTP tends to be faster but is generally considered obsolete by today’s standards and has multiple documented vulnerabilities.
SSTP can be a little more complicated to set up and manage than PPTP, but it’s more reliable overall. Its usage of port 443 means it may sometimes be more effective at bypassing firewalls and other restrictions, while PPTP uses TCP port 1723, which can cause some connectivity issues.
SSTP vs. WireGuard
WireGuard brings numerous benefits over SSTP. Firstly, like OpenVPN, this is an open-source VPN protocol. It’s also lightweight, famed for its very small codebase consisting of as little as 4,000 lines of code. This means that WireGuard runs well even on simpler and weaker devices, is easy to audit, and boasts efficient performance.
WireGuard also has the edge in security, since its small codebase is easily auditable and has fewer vulnerabilities. Plus, it uses state-of-the-art cryptographic algorithms, like ChaCha20, to keep data safe in transit.
WireGuard also uses UDP rather than TCP for lower latency and faster performance when gaming, streaming, making voice and video calls, and so on (though this does make it worse for file sharing). Additionally, this protocol is built into Linux and works well on Windows and other platforms, so it tends to be a better option than SSTP in almost every situation.
SSTP vs. SoftEther
SoftEther is a free and open-source VPN protocol that was officially released in 2014. This makes it significantly newer than SSTP, and its open-source nature makes it a more transparent option, with developers able to examine the code and look for any vulnerabilities.
Designed to be flexible and speedy, SoftEther works equally well on a wide range of platforms, while SSTP is more Windows-oriented. SoftEther also supports a broad range of ciphers and tends to be faster, thanks to its UDP acceleration, so it generally outperforms SSTP in the most important metrics.
SSTP vs. Lightway
Lightway was developed by ExpressVPN. It’s open source and independently audited, and it uses the lightweight wolfSSL library, combined with either 256-bit AES or ChaCha20 encryption, making it a more secure choice than SSTP. Lightway also offers additional security layers, like perfect forward secrecy (PFS), which is also present in OpenVPN, WireGuard, and certain other protocols.
Like other VPN protocols discussed above, Lightway can run over UDP or TCP, while SSTP is limited to TCP only. This makes Lightway more flexible and faster, so it’s a superior option for activities like streaming, gaming, and any other activities that involve a large amount of data flowing between the server and the client.
Regarding compatibility, Lightway is available in ExpressVPN apps for Windows, Linux, macOS, Android, iOS, and routers, so you can quickly and easily set it up and enjoy the same levels of performance across any device. While SSTP works well on Windows, it can be awkward to configure on other platforms.
What is an SSTP VPN?
An SSTP VPN is a virtual private network formed using the Secure Socket Tunneling Protocol. You can set up an SSTP VPN via the built-in VPN client with Windows or with the aid of third-party apps and clients on other platforms.
When to use an SSTP VPN
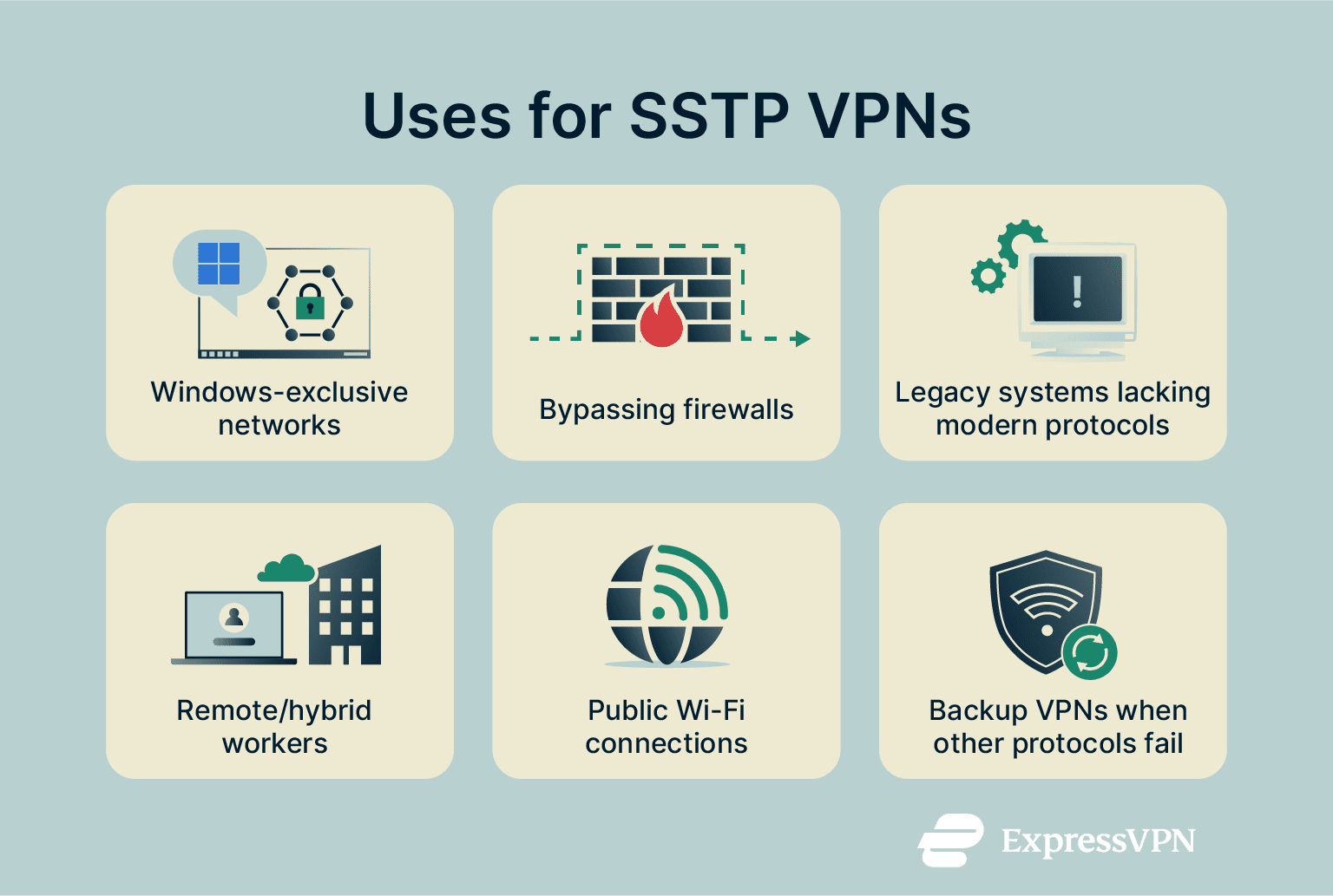 With so many other VPN protocols available, many of which offer superior standards of speed and security than SSTP and better compatibility with other platforms, there aren’t that many use cases for SSTP VPNs nowadays. Still, you may like to set up an SSTP VPN in the following scenarios:
With so many other VPN protocols available, many of which offer superior standards of speed and security than SSTP and better compatibility with other platforms, there aren’t that many use cases for SSTP VPNs nowadays. Still, you may like to set up an SSTP VPN in the following scenarios:
- Windows-centric networks: Since SSTP was designed for the Windows platform, it’s one of the better VPN protocols to use on Windows computers and laptops. If your network is made up entirely of Windows machines, you could consider an SSTP VPN.
- Bypassing firewalls: SSTP runs over TCP, and can use port 443 (the same port as HTTPS), which is commonly open on many networks. This can make it easier to traverse some firewalls compared with protocols that rely on UDP, but it’s not guaranteed to bypass all firewall restrictions.
- Legacy systems: SSTP can also prove useful when you’re trying to establish a secure VPN connection on older infrastructure and legacy devices, especially if more modern protocols like WireGuard aren’t compatible with them.
- Other cases: SSTP can also prove useful for remote workers needing access to corporate networks or users wanting to secure their data when connecting to public or unsecured Wi-Fi. However, in such situations, it’s often better to opt for other, stronger VPN protocols instead, and only use SSTP as a backup if other protocols fail or aren’t available.
How to connect to an SSTP VPN
You can set up your own SSTP VPN connection quite easily on a Windows machine using the built-in Windows VPN settings or with the aid of third-party clients and software on other platforms, like Linux and macOS. The following sections will provide detailed instructions for all three platforms.
Step-by-step guide to setting up SSTP on Windows
Windows users will find it easiest to set up SSTP VPNs, since SSTP was designed by Microsoft with Windows in mind. You don’t need to download any extra software; simply follow these steps to get started:
- Open the Settings on your Windows computer by either using the keyboard shortcut (Windows + I) or finding the Settings icon in the Start menu. Then, select the Network & internet option.
- Click on VPN.
- Click the Add VPN button in the top-right corner.
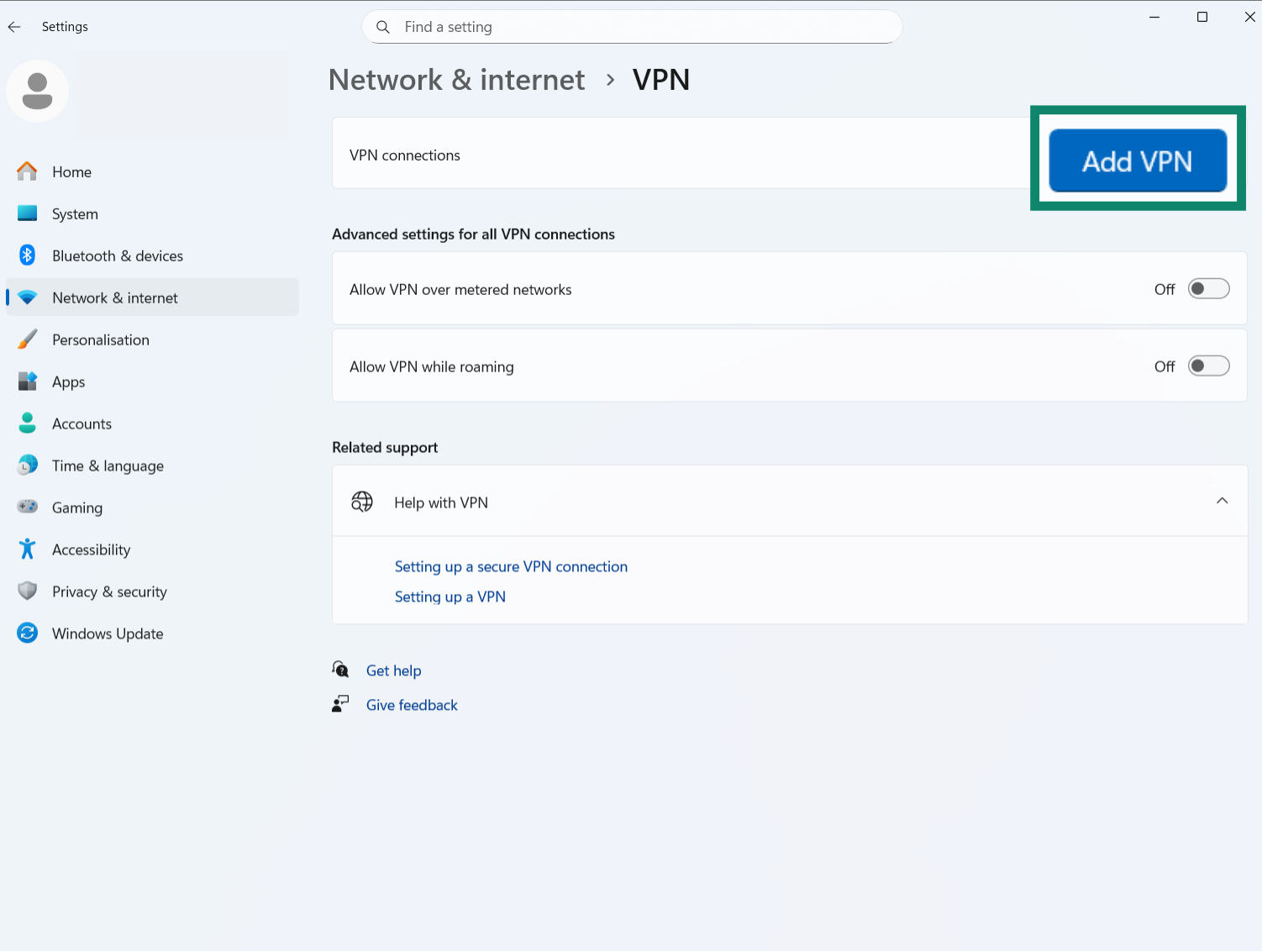
- Enter the details of your SSTP VPN connection, including a name for the connection, plus a server name or address. Make sure you choose Secure Socket Tunneling Protocol (SSTP) in the drop-down VPN type list, then hit the Save button.
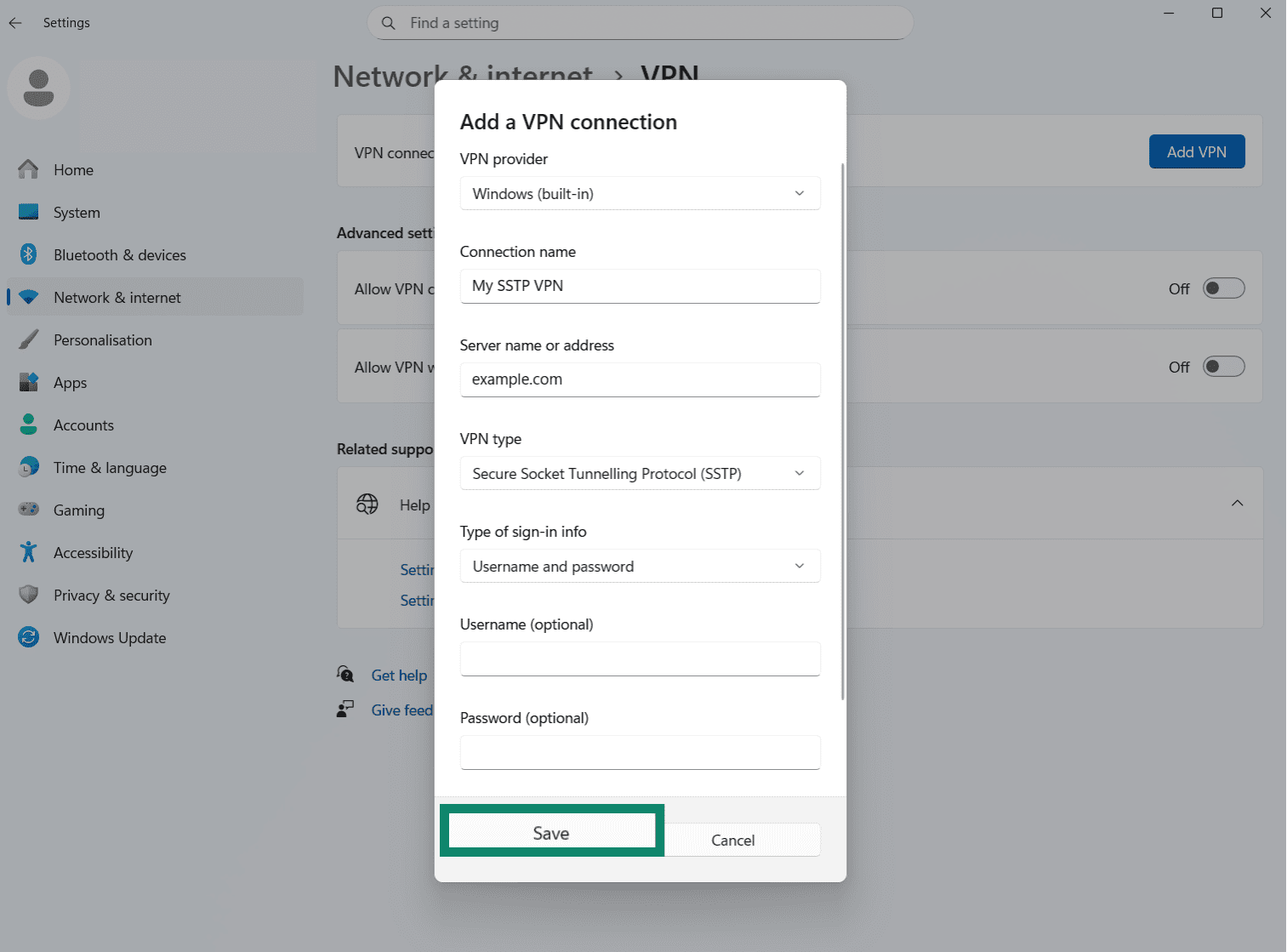
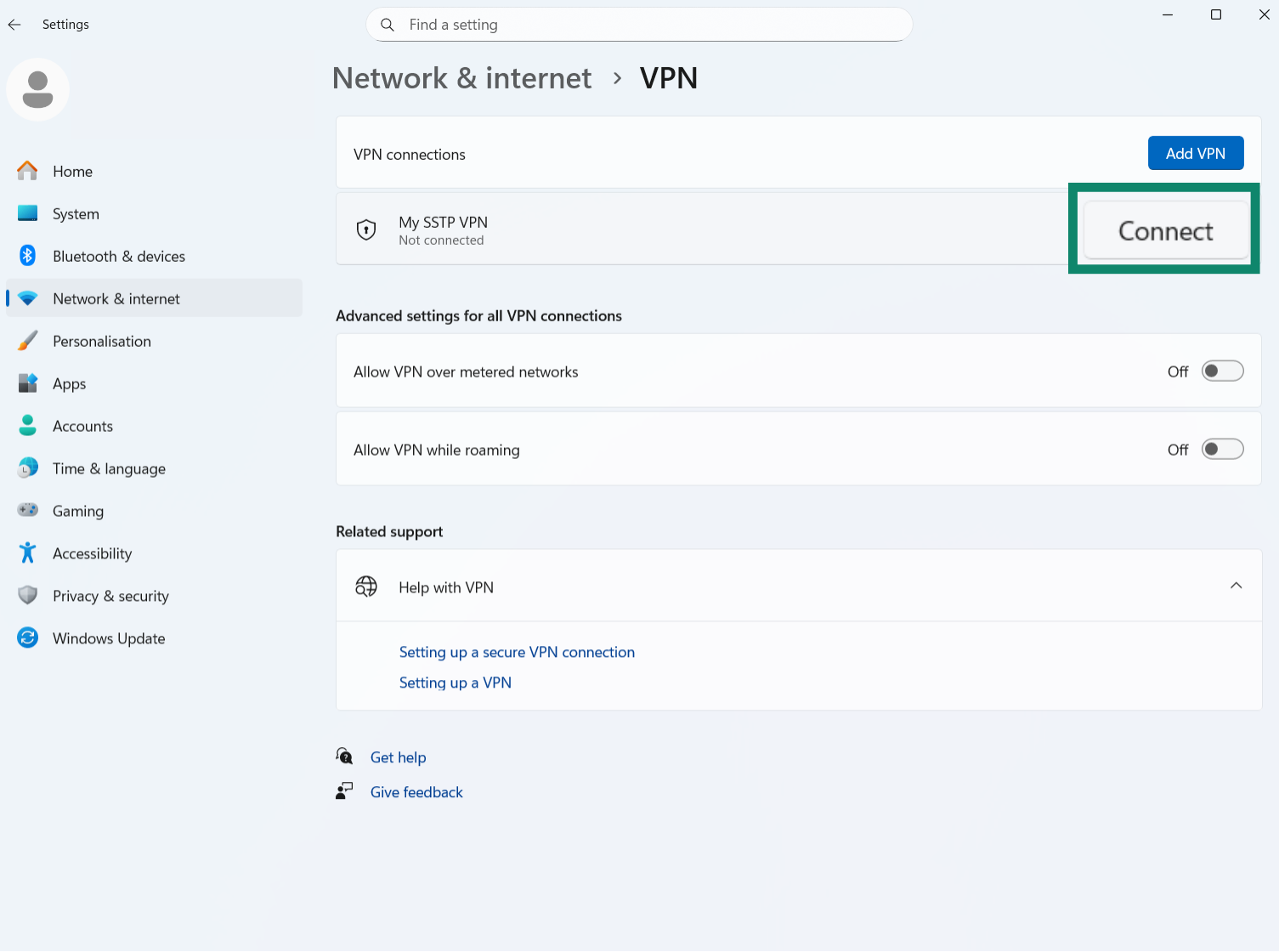
- Back in the VPN menu, find your new SSTP VPN connection in the list and click the Connect button.
How to configure SSTP on Linux and macOS (with third-party clients)
To set up a VPN with SSTP on Linux, follow these steps:
- Open Terminal with the Ctrl, Alt, and T shortcut and run the following command: sudo add-apt-repository ppa:eivnaes/network-manager-sstp.
- Update your system package list using this command: sudo apt update sudo apt upgrade.
- Install the SSTP client with the aid of the special package manager for your distro. On Debian/Ubuntu, the command is as follows: sudo apt install sstp-client.
- Open Network Manager and click on Edit Connections.
- Click the + icon to add a new VPN connection.
- Select Import a saved VPN configuration, then click Create.
- Open the saved VPN configuration file. Select Secure Socket Tunneling Protocol (SSTP) as the VPN type, enter a name for your VPN connection, add the hostname or IP address in the Gateway field, and add the account credentials in the User name and Password fields. Then, click Save.
- To connect, open Network Manager, find the SSTP VPN connection, and click Connect.
For installations on Mac, here are the steps to follow:
- Install the third-party Homebrew package manager for macOS.
- Run the terminal and install the sstp-client package by running this command: brew install sstp-client.
- Run the following command, including your username, password, and IP address in the relevant sections: sudo sstpc --log-stderr --cert-warn --user "USERNAME" --password "PASSWORD" "IP_ADDRESS" usepeerdns require-mschap-v2 noauth noipdefault defaultroute refuse-eap noccp.
- Your traffic will now be routed through the VPN tunnel.
Troubleshooting common SSTP VPN connection issues
Despite being a generally stable and secure VPN protocol, SSTP connections can encounter some issues from time to time, like performance problems or difficulties establishing and maintaining a connection. These handy troubleshooting tips and tricks may help resolve some of the more common issues you encounter:
- Ensure TCP port 443 is open and not being intercepted or disrupted by any proxies or firewalls.
- Make sure TLS versions and cipher suites match at both the client and server ends, which you can do using third-party developer tools to perform handshake simulations or monitor network traffic to identify and diagnose any errors.
- Always check that your device has a stable and reliable internet connection before attempting to connect to a VPN server.
- Reboot your device and/or your router if you can’t connect.
- Keep your operating system and any VPN clients you’re using up-to-date.
- Double-check your user credentials if you have any issues accessing an SSTP VPN server.
FAQ: Common questions about SSTP
What is meant by SSTP?
SSTP stands for Secure Socket Tunneling Protocol. It’s a VPN protocol, or set of rules that govern how secure VPN connections form between devices and servers, helping users enjoy the privacy and security advantages of VPN technology.
How is SSTP used?
The Secure Socket Tunneling Protocol (SSTP) is used to create secure VPN connections. It does this by making an encrypted tunnel between the user’s device and the VPN server, leveraging Secure Sockets Layer (SSL) / Transport Layer Security (TLS) security to keep data safe as it travels from one end to the other.
Is SSL the same as SSTP?
No, SSL stands for Secure Sockets Layer, which is the precursor to Transport Layer Security, or TLS. SSL/TLS is a security protocol for encrypting web traffic. SSTP, meanwhile, stands for Secure Socket Tunneling Protocol and is a VPN protocol for establishing secure VPN connections between devices and servers. The two share some similarities, and SSTP relies on the security of SSL/TLS to encrypt data.
Does SSTP use HTTPS?
Yes, the Secure Socket Tunneling Protocol (SSTP) uses an HTTPS connection to encapsulate Point-to-Point Protocol (PPP) traffic. It runs on the same port (port 443) as HTTPS, which also makes it decent for bypassing firewalls, proxies, and web restrictions.
Is SSTP only for Windows?
No, the Secure Socket Tunneling Protocol (SSTP) is not just for Windows, but this is a common misconception because SSTP was made by Microsoft and designed primarily for the Windows operating system. SSTP is also native to Windows and easiest to use on Windows devices, but it can function on other systems, such as Linux, Android, and macOS, courtesy of third-party software.
Which port is used by SSTP?
The Secure Socket Tunneling Protocol (SSTP) uses Transmission Control Protocol (TCP) port 443 to secure its VPN connections. Port 443 is also used for HTTPS traffic, which makes it essential for secure web browsing. As such, port 443 tends to be open by default on most networks, and this allows SSTP to quite easily bypass firewalls and network restrictions that might cause problems on other ports.
What is the Open SSTP Client?
The Open SSTP Client is an open-source Android app that allows users of Android mobile devices to connect to secure Secure Socket Tunneling Protocol (SSTP) VPN servers, essentially making the SSTP protocol more accessible for mobile users. It’s available on the Google Play Store.
Is SSTP better than OpenVPN?
In most metrics, no; the Secure Socket Tunneling Protocol (SSTP) is not better than OpenVPN. OpenVPN has the distinct benefits of being open source and cross-platform, while SSTP is closed-source and only natively supported on Windows, though it can run on other platforms. OpenVPN also offers superior security and a wider range of configuration options.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN